Every day, businesses are generating more and more data. This data is generated by employees, customers, and machines. And it’s not just limited to companies—government organizations and non-profits are also sitting on a goldmine of potentially sensitive business data.
While this data can be used to gain insights into how a business is performing or where it can improve, it also poses a risk. This is where data risk management comes in.
What is Data Risk Management?
Data risk management is the process of identifying, assessing, and mitigating the risks associated with data. This includes risks related to its confidentiality, integrity, and availability.
Data could be anything from both digital and physical data, such as customer information, financial records, employee files, etc. A comprehensive data risk management strategy will take all of these into account and put measures in place to protect your data from these risks.
In order to minimize data risk exposure, businesses need to have a clear understanding of what data they have, where it’s stored, and who has access to it. They also need to put processes and controls in place to protect this data from unauthorized access or modification.
How is Data At Risk?
Data can be at risk for a number of reasons.
-One reason is that data can be lost or corrupted. This can happen if a computer crashes or if a file is accidentally deleted.
-Another reason is that data can be accessed by unauthorized individuals. This can happen if a computer is hacked or if an individual guesses another person’s password.
-Data can be misused. This can happen if an individual uses data for a purpose that it was not intended for, such as using personal data to solicit marketing materials.
-Data is also at risk because it is often stored in insecure locations, such as on a hard drive or in the cloud. This means that if the location is compromised, the data may be compromised as well.
-Another data-related risk is poor data governance. It can lead to a host of problems, including inaccurate reporting, duplicate records, and inconsistent data. In addition, poorly governed data is often more difficult and costly to maintain.
-When data management occurs, it can have serious consequences, ranging from financial loss to identity theft to damage to a company’s reputation and intellectual property.
As you can see, there are many ways in which data can be at risk. It is important to take steps to protect your data, such as backing up files and encrypting sensitive information.
Why Do Businesses Need to Invest in Data Security?
Data security is crucial for any business or organization that relies on electronic data. Without proper security measures in place, sensitive information can be leaked, stolen, or simply lost.
This can lead to financial losses, damage to reputation, and a loss of customer trust. In some cases, it can even lead to legal penalties. Data security is therefore essential for protecting your business or organization’s most valuable assets.
There are many different aspects to data security, but some of the most important include encryption, access control, and backups.
- Encryption helps to ensure that data cannot be accessed by unauthorized individuals.
- Access control measures help to restrict who can access sensitive data.
- And backups provide a safety net in case data is lost or damaged.
By taking these steps, you can help to keep your business or organization’s data safe and secure.
Do you need help with data risk management?
Contact Growth Hackers
What Are the Benefits of Data Risk Management?
Organizations that practice data risk management can enjoy a number of benefits.
- They can avoid the costly consequences of data breaches, such as reputational damage, legal liability, and loss of customer trust.
- They can improve their overall security posture by identifying and addressing vulnerabilities in their systems.
- They can make better decisions about where to allocate scarce resources by understanding the risks associated with different kinds of data.
What Are the Best Practices of Data Risk Management?
Managing data risk is a critical component of any organization’s overall security strategy. There are a number of best practices that should be followed in order to effectively manage data risks.
- One of the most important is to establish clear ownership and responsibility for data security. This means assigning specific roles and responsibilities for managing data risks and protecting sensitive data within the organization.
- It is important to create and implement clear policies and procedures for handling data. These should be designed to protect data from unauthorized access, use, and disclosure.
- Regular monitoring and auditing of data security should be conducted in order to identify potential risks and take corrective action as needed.
- Companies should encrypt all sensitive data. This will make it much more difficult for hackers to access the information.
- Companies should invest in good security software and keep their systems up to date with the latest security patches. It helps to classify data according to its sensitivity level.
- Access to personally identifiable information should be restricted to only those who need it, and all user activity should be logged and monitored.
- All data should be backed up regularly to minimize the impact of data loss.
- Data optimization should be done on a regular basis to keep up with the latest trends and best practices.
How Do You Efficiently Carry Out Data Risk Management in Business Operations?
Data risk management encompasses all the activities and controls that are put in place to protect data from unauthorized access, theft, or destruction. When carried out effectively, data risk management can help businesses to minimize the impact of data breaches, meet regulatory requirements and safeguard their reputation.
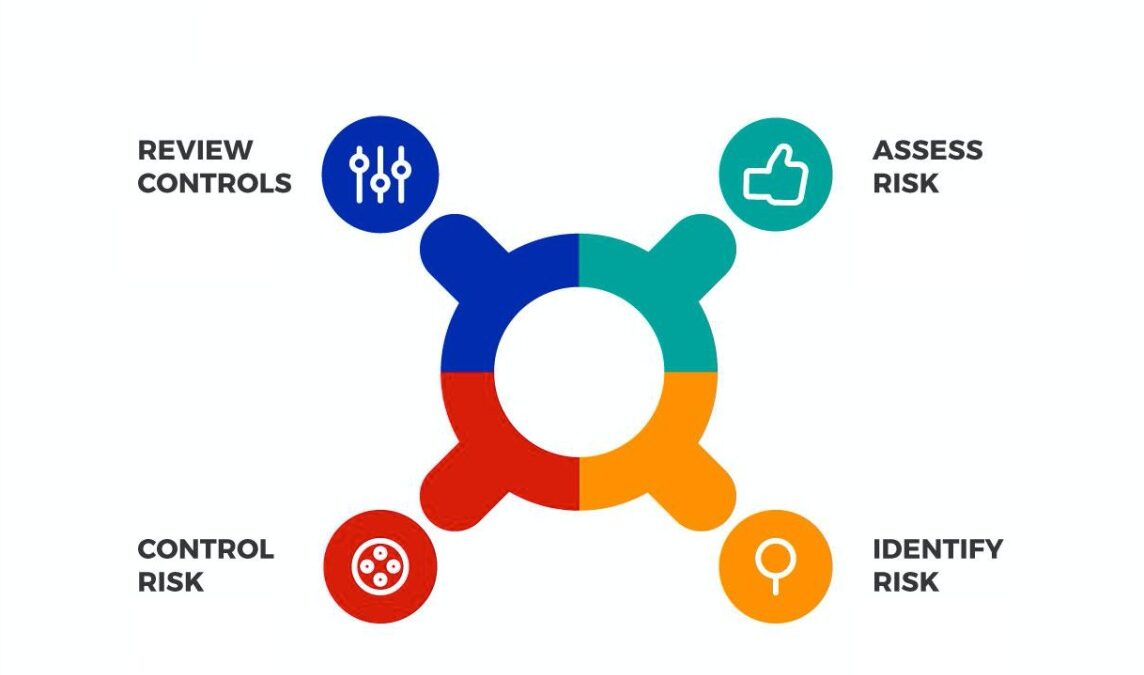
There are four crucial steps that businesses can take in order to effectively carry out data risk management practices.
1. Identification
The first step is to identify all the potential risks to your data. This includes both internal and external threats. Internal threats could include employees accidentally deleting or modifying data, while external threats could include cyber attacks or natural disasters.
So, how can you tell when risk is looming? Here are a few red flags to watch out for:
Unexplained changes in data patterns
If you suddenly notice a spike in errors or unexpected variations in your data, it could be a sign that something is wrong.
Lack of visibility into data
If you can’t track where your data is coming from or how it’s being used, it’s harder to spot potential issues.
Reliance on manual data processes
If your data management relies heavily on manual processes, it’s more likely that something will go wrong at some point.
A few ways you can counter potential risk exposure in data management are as follows.
-Make sure you have a clear understanding of your organization’s data landscape. Know where your data is coming from, where it’s stored, and who has access to it. This will help you identify any potential weak points in your system.
-Periodically review your data security protocols and make sure they are up to date. This includes ensuring that all sensitive data is encrypted and that only authorized users have access to it.
-Stay up to date on the latest security threats and trends. This way you can be proactive in identifying and addressing any new risks that may arise.
Get ready to implement data risk management in your business operations today!
2. Assessment
Once you’ve identified all the potential risks, you need to assess how likely they are to occur and what impact they would have on your business if they did occur. And the best way to do this is by conducting a data risk assessment.
This will help you identify which areas of your business are most at risk and what controls you need to put in place to mitigate those risks. A data risk assessment should consider all aspects of your business, from how you collect and store data to how you use it and share it with third parties. It should also take into account the potential impact of a data breach, both on your business and on your customers.
However, assessing risks when carrying out data risk management can be a daunting task. Here are some key considerations that can help you to assess risks effectively.
First, consider the types of data that you are storing and processing. What are the sensitivity levels of this data? Is it critical to your business operations? How easy would it be to replace if lost or stolen? These are all important factors to consider when assessing risk.
Next, consider the potential consequences of a data breach. What could an attacker do with your data? Could they access sensitive customer information? Could they disrupt your business operations? Understanding the potential impacts of a data breach will help you to prioritize risks and put mitigation measures in place.
Finally, keep a close eye on the external environment and trends in the cybersecurity landscape. By understanding the current threats, you can be better prepared to protect your data against them.
3. Mitigation
The next step is to put measures in place to mitigate risk. For example, you might implement firewalls and security measures to protect against cyber attacks or back up your data regularly to guard against accidental deletion or modification.
Risk mitigation is an ongoing process that requires constant vigilance and attention. When it comes to data risk management, there are a few key strategies that can help to mitigate the risk of data loss or theft.
-One common strategy is known as “defense in depth.” This approach involves implementing multiple layers of security controls, such as firewalls, intrusion detection systems, and encryption.
-Another strategy is known as “least privilege.” This approach involves limiting access to data to only those users who need it.
-Thanks to commercial risk management, organizations can establish protocols and procedures for handling sensitive data. This can help to ensure that only authorized personnel have access to the data and that it is properly safeguarded at all times.
-Another effective strategy is to encrypt data files. This makes it much more difficult for unauthorized individuals to gain access to the information, and can help to protect the data even if it falls into the wrong hands.
-Finally, regular backups of data can be extremely helpful in mitigating the risks associated with data loss or corruption. By keeping multiple copies of important files, businesses can minimize the impact of any one incident.
By using a combination of these and other strategies, businesses can effectively reduce the risks associated with managing their data.
4. Monitoring
When it comes to data risk management, ongoing monitoring is essential in order to ensure that strategies are effective and aligned with organizational goals. Utilizing tools like DSPM can help automate the monitoring of data security measures and ensure compliance with industry standards. There are a few key factors to keep in mind when carrying out this monitoring.
First, it is important to track metrics around data protection, such as the number of data breaches or incidents of unauthorized access. This can help to identify where weaknesses exist in the system and what needs to be improved.
Second, it is also necessary to monitor compliance with data security policies and procedures. This ensures that everyone in the organization is adhering to the same standards and helps to prevent accidental breaches.
Finally, it is also important to review the effectiveness of data risk management strategies on a regular basis. This helps to ensure that they are still relevant and effective in the ever-changing landscape of data security.
By monitoring these factors, organizations can ensure that their data risk management strategies are effective and up-to-date.
Final Thoughts on What is Data Risk Management and How To Do It Properly
Data risk management is an essential process for any organization that relies on data. By taking the time to properly identify and assess risks, and put in place effective mitigation strategies, organizations can protect their data from harm.
As a business owner, you are probably always looking for ways to optimize your marketing efforts and get the most bang for your buck. Enter Growth Hackers.
We are a full-service digital marketing agency that can help you with all aspects of your online presence, from website design and development to social media marketing to search engine optimization (SEO).
And because we are a data-driven company, we can also help you efficiently protect & nurture your data life cycle and carry out data risk management so that you can make informed decisions about your marketing strategy. In other words, Growth Hackers can help you save time and money while still getting great results.
So, if you’re looking for a one-stop shop for all your digital marketing needs, contact Growth Hackers team now.